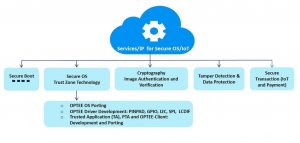
Security IP Suite
The Embedded systems targeted and designed for a specific application need, gets connected to internet. Many of the tasks, computations and applications accomplished in Desktop PC are achieved through embedded device as well. Thus, leaving the devices vulnerable to attacks, which leads to the necessity to address the issues of design constraints and limitations in hardware to provide a cost-effective solution. Secured systems are-
- Protected from external threats
- Should be confidential
- Only authenticated program should able to run in the system
iWave offers Services and IP for secure OS / IoT:
- Secure Boot
- Secure OS – TrustZone Technology
- OPTEE OS Porting
- OPTEE Driver Development: PINPAD, GPIO, I2C, SPI, LCDIF
- Trusted Application (TA), PTA and OPTEE-Client: Development and Porting
- Image Authentication and Verification (Cryptography)
- Tamper Detection & Data Protection
- Secure Transaction (IoT and Payment
Why Security is Important ….??!
The immense need to address this security in Embedded Systems, invades following protection of data:
- Private Data: If security is compromised, end user is impacted directly. For example, in case of internet banking passwords.
- Restricted Data: If security is compromised, the content provider is impacted heavily. For example, digital multimedia content such as copyrighted digital photos, audio and video contents.
In connected devices, this secure data is transferred through public networks. So, it is important to ensure that secure data is protected from unauthorized access thus ensuring security.
WolfSSL SSL/TLS Library
iWave have partnered with wolfSSL Inc, a popular USA based embedded SSL/TLS and cryptography provider for the IoT. The partnership allows iWave to add the benefits of wolfSSL embedded SSL/TLS library and hardware crypto support onto several iWave devices (such as SOMs, Dev. Boards, and SBCs) that include hardware cryptography modules. The partnership expands iWave’s commitment to providing our customers with a completely secure embedded platform optimized to meet the performance specifications of connected IoT solutions.
The wolfSSL embedded SSL library is a lightweight, portable, C-language-based SSL/TLS library targeted at IoT, embedded, and RTOS environments. wolfSSL advanced feature set, size, and speed make it work seamlessly in desktop, enterprise, and cloud environments. iWave devices with the wolfSSL stack are well balanced to deploy in connected space and well supported with a strong engineering team to help customers through product development and deployment cycles.
Highlights:
- wolfSSL supports industry standards up to the current TLS 1.3 and DTLS 1.2
- Up to 20 times smaller than OpenSSL
- Offers a simple API, an OpenSSL compatibility layer, OCSP, and CRL support
- backed by the robust wolfCrypt cryptography library
iWave Expertise in wolfSSL:
- Stack integration
- Optimized configuration tuning based on the requirement
- Middleware/API development on top wolfSSL stack for application developer’s easiness
- Debugging skill
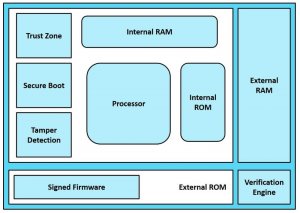
Security in Embedded System:
Security in Embedded System is mostly a combination of Hardware, Software, and Mechanical solutions. A hardware solution is like Secure SoC, Secure ROM, TrustZone, Hardware Cryptography, Tamper Detection, etc. The software solution includes software encryption algorithms, Trusted Software. In most cases it will be a combination of Hardware and Software solutions to ensure the highest security.
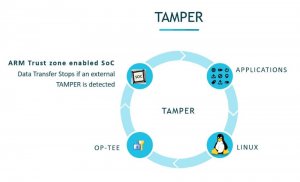
Tamper Detection:
Tamper Detection module will provide physical protection for the devices. In case of any tampering, the Tamper detection modules inform the SoC of the corresponding events as below
- External Tamper
- External PIN
- Internal Tamper
- Voltage
- Temperature
- Clock
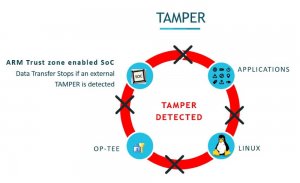
When the SoC detects the tampering event, a security violation alarm is asserted for
- Software Action
- Security hardware present in SoC does the following
- Will deny access to any of the modules (data transfer)
- All secure memory contents (Eg: Secured Keys) stored in the internal RAM will be erased
Secure Boot:
Many SOC manufacturers provide a “Secure Boot” option which adds cryptographic checks to each stage of the Secure boot process. The firmware code is signed using the device manufacturer’s code verification private key. The Secure Bootloader, on boot up, checks the validity of the code by verifying the signature using the code verification public-key.
Cryptographic signature algorithms:
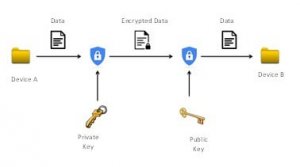
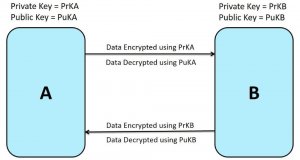
Cryptographic algorithms are used to encrypt and decrypt the data. Most famously used Cryptographic algorithms are public key- private key cryptographic algorithms. This algorithm uses two different but mathematically linked keys.
- Before sending it to another device, the Private key is used to encrypt the data and generate the encrypted data.
- The public key is shared with everyone. The decryption algorithm uses this public key to decrypt the encrypted data and obtain the original data.
A similar Cryptographic algorithm approach is used in the secure boot with few enhancements. Here along with cryptographic algorithms, certain measures are taken so that the system cannot be hacked.
In Secure Boot, the Public key is encrypted and stored in one-time programmable registers.
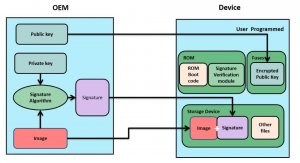
ROM code contains a signature verification module and the code verification public-key to verify the firmware code.
- Generate a private key and public key using the device manufacturer’s code.
- The image is signed with the device manufacturer’s private key using a signature algorithm. This signed image is programmed to the storage devices.
- The public key is encrypted and burned to fuses.
- The ROM code, on boot up, checks the validity of the signed image by verifying the signature using the public key.
- If the signature is valid, then the image will boot. Otherwise the board will fail to boot.
Why it is Secure…!!!
- ROM code resides in a write-protected ROM. This ensures that the Secure Boot loader itself is never modified.
- The private key is always kept secret by the device manufacturer.The public key does need to be stored within the device in a manner so that it cannot be replaced by a public key that belongs to an attacker. This is done by writing the public key to one-time programmable registers.
- The public key is also encrypted before writing to one-time programmable registers. This ensures that only the device manufacturer’s “signature verification code” can decrypt it and use it to verify the signed image.
Chain of Trust:
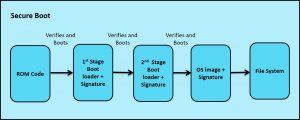
A secure boot checks for “authenticated image” in every stage of the boot process. This process aims to check the integrity of the “authenticated image”, hence preventing any unauthorized software from running.
The secure boots rely on the idea of “Chain of Trust”. Starting with an implicitly trusted component, every other component can be authenticated before being executed, hence always only authenticated trusted image is running.
ROM code verifies & authenticates the signed 1st stage boot loader.
The 1st stage boot loader verifies & authenticates the signed 2nd stage boot loader.
The 2nd stage boot loader verifies & authenticates the signed OS image followed by file system mounting and launching the application.
ARM TrustZone:
Arm TrustZone technology is a System on Chip (SoC) and CPU system-wide approach for security. TrustZone is hardware-based security built into SoCs by semiconductor chip designers who want to provide secure endpoints and a device root of trust.
Trusted OS like OPTEE (Open Portable Trusted Execution Environment) runs securely on Trustzone hardware embedded in the SoC. The processor core of SoC has two virtual cores: Secure and Non-Secure
- The secure world runs Trusted OS like OP-TEE – ARM Trusted Zone
- The non-Secure world runs Rich OS like Linux (REE) – ARM Cortex-A
The Secure Boot loader (ROM) in the SoC ensures that the device boots up with the Secure OS/firmware with the right process privileges. The Memory Management Unit (MMU) configured by the OS permits access to the buffers in the Internal RAM that involves secret key operations only to the secure processes with special OS privileges.
OP-TEE OS running in TrustZone provides key features like isolation from REE, small footprint, and portability.
For more details, information about OPTEE OS refer: Here
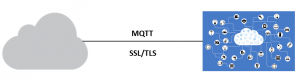
Secure IoT:
IoT Communication with the cloud over MQTT is secured with SSL/TLS. Every data transfer will be encrypted using TLS protocol. Apart from SSL/TLS, Cloud may have its own authentication methods and policies to allow/restrict the connection.
Related Article
Security Optimized Embedded Solutions