- Products
- Automotive
- Avionics
COTS Module
- Agilex 7 SmartNIC Card
- Zynq RFSoC ADC DAC PCIe Card
- ZU7/ZU5/ZU4 PCIe SmartNIC Card
- ZU19/17/11 PCIe SmartNIC Card
- PCIe Switch Module
- PCIe to SD 3.0 M.2 Module
- Kintex-7 PCIe Card
- Zynq ZU7/ZU5/ZU4 3U-VPX
- Virtex UltraScale+ 3U VPX
- Kintex UltraScale+ 3U VPX
- Zynq ZU19/17/11 3U VPX
- Kintex-7 3U VPX Card
- VITA 57.4 FMC+ Loopback Test Module
- VITA 57.1 FMC Loopback Test Module
- PCIe Gen4 x8 FMC Module
- PCIe Gen4 x16 FMC+ Module
- PCIe Gen3 x8 FMC Module
- Quad QSFP28 FMC+ Module
- FMC Add-On Cards
- IP Cores
- ODM Solutions
- Custom Design
- Company


Get a Quote
Please fill in the form and we will get back to you soon!
We appreciate you contacting iWave.
Our representative will get in touch with you soon!

Get in Touch
We appreciate you contacting iWave.
Our representative will get in touch with you soon!
Thank you for subscribing to our newsletter!
Security Suite for TCU
A leading Digital Transformation Enterprise providing connected mobility solution and intelligent transportation solutions secured and protected their Telematic Control Units against attacks and malware.
Client Background
A North American Enterprise, a global leader providing intelligent transportation solutions.
The client was looking at a vendor who has experience on the automotive solutions and embedded systems expertise helping prevent unauthorized access to the device with a balance in the performance, efficiency, and reliability.
The Challenge
With the requirement to secure telematic units against potential attacks and hackers taking control of the vehicles, the enterprise required quick implementation of secure boot and secure filesystem on their existing units.
The TCU which connects to the ECU of the vehicle provides a very rich gateway for hackers to penetrate the car’s network
- Secure Boot
- Secure Filesystem
- OS Hardening
- NXP i.MX 6
- Wi-Fi Security
- Easy to use API
Solution
iWave Systems, with vast expertise in automotive solutions and embedded systems, was chosen as the telematics device partner and implementation of the security features .
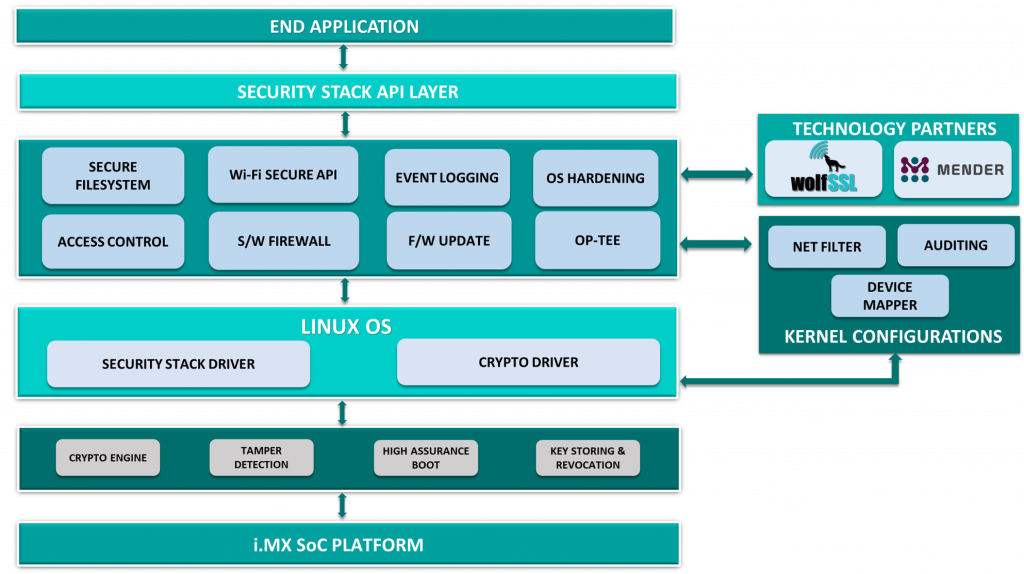
iWave Systems introduced a Security suite which secures connected devices, enabling them with security functions such as encryption, storage, data transmission and certificate management. The easy to integrate solution helps address the security challenges creating a safe and secure environment. Security Suite includes secure boot, Wi-Fi secure API, event logging, OS hardening, access control, software firewall and secure firmware update to name a few.
Our security architecture was developed to protect the integrity of the firmware. This means that even if a malicious actor manages to hack the device, they will be unable to interfere with the firmware. Thus, reduces the complexity and huge financial loss in terms of the data that can be lost.
Implementation
Secure File System takes an end-to-end approach of protecting data by cryptography preventing unauthorized access to the data storage. The entire file system is encrypted. So, Without proper encryption keys, data stored on any encrypted file system cannot be read (decrypted). Root file system is booted with read-only mode and write permission is given in a controlled way.
iWave is an embedded systems engineering and solutions company, designing solutions for the Industrial, Medical, Automotive and Avionics vertical markets, and building on our core competency of embedded expertise since 1999. Read More…
Newsletter
Copyright © 2022 iWave Systems Technologies Pvt. Ltd.

